Web Application Firewall
A simple solution to deploying and maintaining your application layer security solution
Protect web apps from exploits compromising security, availability, or resource use.
 |
Build MoreUse managed rules to save time and focus on developing your applications. |
 |
Block Bots
Easily detect, block, or limit common bots to protect your site.
|
 |
Traffic InsightsGain better control and visibility over web traffic with detailed metric emissions. |
Protect your web applications from common exploits
With AWS WAF, you can create security rules that control bot traffic and block common attack patterns such as SQL injection or cross-site scripting (XSS).
At Nebulane, as an AWS WAF Delivery Partner, we specialize in securing your web applications against common web exploits. Our expertise ensures that your applications are safeguarded from threats that could compromise security, affect availability, or consume excessive resources. By partnering with Nebulane, you can enhance your application’s security posture and create custom rules to block attacks like SQL injection and cross-site scripting.
How It Works
AWS WAF shields your applications from common web threats and bots, safeguarding availability, enhancing security, and preventing excessive resource use.
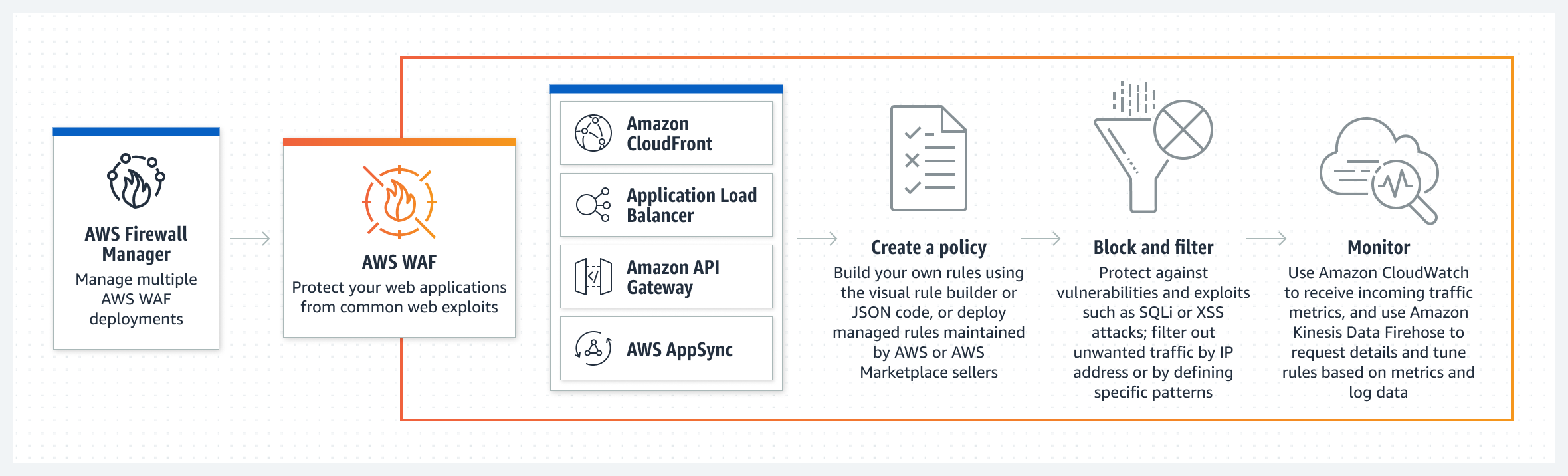
AWS Web Application Firewall Use Cases
 |
E-commerce Site Protection
AWS WAF blocks malicious requests before they hit your site. |
 |
API Protection
AWS WAF shields APIs from cyberattacks like brute force and phishing attempts. |
 |
Web Application Protection
AWS WAF defends web applications against cyberattacks like SQL injection and cross-site scripting (XSS). |
 |
Content Filtering
AWS WAF can filter website content by blocking requests with specific unwanted words or phrases. |
 |
DDoS Protection
Integrate AWS WAF with AWS Shield to guard your applications against Distributed Denial of Service (DDoS) attacks. |
 |
Custom Rule Creation
Tailor AWS WAF rules to block or allow requests based on patterns, IP addresses, or user agents. |
